𝐒𝐭𝐫𝐞𝐧𝐠𝐭𝐡𝐞𝐧𝐢𝐧𝐠 𝐂𝐲𝐛𝐞𝐫𝐬𝐞𝐜𝐮𝐫𝐢𝐭𝐲: 𝐓𝐡𝐞 𝐆𝐫𝐨𝐰𝐢𝐧𝐠 𝐑𝐨𝐥𝐞 𝐨𝐟 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐧𝐝 𝐀𝐜𝐜𝐞𝐬𝐬 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 (𝐈𝐀𝐌) 𝐒𝐨𝐥𝐮𝐭𝐢𝐨𝐧𝐬
The identity and access management market size was valued at USD 15.93 billion in 2022 and is projected to expand at a compound annual growth rate (CAGR) of 12.6% from 2023 to 2030.
Identity and access management (IAM) assures that the appropriate person and job position (identities) in an organization have access to the tools they need to perform their duties.
The rising cases of fraudulent and cybercrime activities are driving organizations to implement IAM systems as a result of the rapid adoption of the cloud and the advancement of new technologies. IAM uses identity analytics and intelligence to monitor unusual user account activity.
 𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐧𝐝 𝐀𝐜𝐜𝐞𝐬𝐬 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 (𝐈𝐀𝐌)
𝐈𝐝𝐞𝐧𝐭𝐢𝐭𝐲 𝐚𝐧𝐝 𝐀𝐜𝐜𝐞𝐬𝐬 𝐌𝐚𝐧𝐚𝐠𝐞𝐦𝐞𝐧𝐭 (𝐈𝐀𝐌)
➼Single Sign-On (SSO)
➼Multi-Factor Authentication (MFA)
➼Role-Based Access Control (RBAC)
➼Privileged Access Management (PAM)
➼Adaptive Authentication
➼User Activity Monitoring
 𝐄𝐧𝐝𝐩𝐨𝐢𝐧𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
𝐄𝐧𝐝𝐩𝐨𝐢𝐧𝐭 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
➼Antivirus and Anti-Malware Protection
➼Endpoint Detection and Response (EDR)
➼Device Compliance Management
➼Mobile Device Management (MDM)
➼Patch Management
➼Disk Encryption
 𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐌𝐢𝐜𝐫𝐨-𝐒𝐞𝐠𝐦𝐞𝐧𝐭𝐚𝐭𝐢𝐨𝐧
𝐍𝐞𝐭𝐰𝐨𝐫𝐤 𝐌𝐢𝐜𝐫𝐨-𝐒𝐞𝐠𝐦𝐞𝐧𝐭𝐚𝐭𝐢𝐨𝐧
➼Virtual LAN (VLAN) Segmentation
➼Software-Defined Perimeter (SDP)
➼Firewall Policies for Micro-Segmentation
➼Zero Trust Network Access (ZTNA)
➼Virtual Private Cloud (VPC) Segmentation
➼Micro-Segmented Zones for IoT Devices
 𝐀𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
𝐀𝐩𝐩𝐥𝐢𝐜𝐚𝐭𝐢𝐨𝐧 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲
➼Web Application Firewalls (WAFs)
➼API Security
➼Runtime Application Self-Protection (RASP)
➼Application Vulnerability Scanning
➼DevSecOps Integration
➼Container Security
 𝐃𝐚𝐭𝐚 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐚𝐧𝐝 𝐄𝐧𝐜𝐫𝐲𝐩𝐭𝐢𝐨𝐧
𝐃𝐚𝐭𝐚 𝐒𝐞𝐜𝐮𝐫𝐢𝐭𝐲 𝐚𝐧𝐝 𝐄𝐧𝐜𝐫𝐲𝐩𝐭𝐢𝐨𝐧
➼Data Encryption at Rest and in Transit
➼Data Loss Prevention (DLP)
➼Access Control Policies for Sensitive Data
➼Data Masking
➼Cloud Data Security Solutions
➼File-Level Encryption
 𝐓𝐡𝐫𝐞𝐚𝐭 𝐈𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞 𝐚𝐧𝐝 𝐀𝐧𝐚𝐥𝐲𝐭𝐢𝐜𝐬
𝐓𝐡𝐫𝐞𝐚𝐭 𝐈𝐧𝐭𝐞𝐥𝐥𝐢𝐠𝐞𝐧𝐜𝐞 𝐚𝐧𝐝 𝐀𝐧𝐚𝐥𝐲𝐭𝐢𝐜𝐬
➼Security Information and Event Management (SIEM)
➼User and Entity Behavior Analytics (UEBA)
➼Threat Intelligence Platforms
➼Intrusion Detection and Prevention Systems (IDPS)
➼AI-Powered Threat Detection
➼Automated Incident Response
➼Identity Governance
➼Directory Services
➼User Lifecycle Management
➼Behavioral Analytics
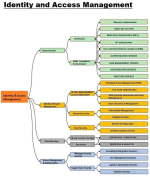
Now, I understand a little more as to why IAM in a part of the new SecurityX cert exam objectives!!!
The identity and access management market size was valued at USD 15.93 billion in 2022 and is projected to expand at a compound annual growth rate (CAGR) of 12.6% from 2023 to 2030.
Identity and access management (IAM) assures that the appropriate person and job position (identities) in an organization have access to the tools they need to perform their duties.
The rising cases of fraudulent and cybercrime activities are driving organizations to implement IAM systems as a result of the rapid adoption of the cloud and the advancement of new technologies. IAM uses identity analytics and intelligence to monitor unusual user account activity.
➼Single Sign-On (SSO)
➼Multi-Factor Authentication (MFA)
➼Role-Based Access Control (RBAC)
➼Privileged Access Management (PAM)
➼Adaptive Authentication
➼User Activity Monitoring
➼Antivirus and Anti-Malware Protection
➼Endpoint Detection and Response (EDR)
➼Device Compliance Management
➼Mobile Device Management (MDM)
➼Patch Management
➼Disk Encryption
➼Virtual LAN (VLAN) Segmentation
➼Software-Defined Perimeter (SDP)
➼Firewall Policies for Micro-Segmentation
➼Zero Trust Network Access (ZTNA)
➼Virtual Private Cloud (VPC) Segmentation
➼Micro-Segmented Zones for IoT Devices
➼Web Application Firewalls (WAFs)
➼API Security
➼Runtime Application Self-Protection (RASP)
➼Application Vulnerability Scanning
➼DevSecOps Integration
➼Container Security
➼Data Encryption at Rest and in Transit
➼Data Loss Prevention (DLP)
➼Access Control Policies for Sensitive Data
➼Data Masking
➼Cloud Data Security Solutions
➼File-Level Encryption
➼Security Information and Event Management (SIEM)
➼User and Entity Behavior Analytics (UEBA)
➼Threat Intelligence Platforms
➼Intrusion Detection and Prevention Systems (IDPS)
➼AI-Powered Threat Detection
➼Automated Incident Response
➼Identity Governance
➼Directory Services
➼User Lifecycle Management
➼Behavioral Analytics

Now, I understand a little more as to why IAM in a part of the new SecurityX cert exam objectives!!!
